In November 2019, I wrote a story on Twitter focused on the business case analysis I performed around implementing a Governance, Risk, and Compliance (GRC) product while in my previous role. (Thread Reader Link).
The story received positive feedback and several people asked me to expand on some of the details and outline it in a blog post for ease of understanding. This blog post will expand even further to discuss the entire business case for implementing a GRC program – people, process, and tools – in an organization. Throughout this post, I will show and discuss screenshots that were used to present my business case to management.
Please keep in mind that I am not one of many GRC experts. This is simply my own story as someone new to this vertical and how I approached it.
Where you are
If you’re like many organizations, you’re utilizing the power of Microsoft Excel and probably some Microsoft Word too. Your policies are word documents saved in PDF format. Your tracking of compliance and gap analysis, and maybe even a Plan of Actions & Milestones (POA&M), if you’re really fancy, is across several spreadsheets.
If that’s the case, don’t judge yourself too harshly. This is the normal path of maturation for many organizations and frequently leads to a successful program. Implementing a GRC product before you’re ready may actually cause your strategy to crash and burn. You need to establish a foundation to grow from and understand the environment before you can accurately perform a proof of concept for any given tool.
With that said, if you’re reading this, it’s likely because you’ve reached the limit of what a manual tracking process can do. How can you reasonably track compliance queries and actions in a spreadsheet? How can you send action items to individuals to question and prove their compliance to a control at scale? How can you save evidence easily? SharePoint works, but the organization capability is minimal and now your spreadsheet is just links to these documents instead of being easily aligned. How are you sending out questionnaires to your vendors to work on your third-party risk management? Are you manually sending an email, follow-up, and tracking every action in a column on a spreadsheet? How do you quickly answer an auditor regarding your compliance? What if a new regulation comes out and you need to answer your compliance quickly? The real question is, how does your program scale when you have several GRC analysts – or more – doing the work?
What you need
The answer is a GRC solution. The intimidating factor that many have around a GRC solution is cost. It doesn’t help that most longstanding institutions are using some of the originals, like Archer and MetricStream. It’s hard to consider a GRC software purchase when you have some insight and know products like those are $1 million or more implementations. Plus, they require consultancy just to get anything done or configured within it to make it usable. However, this is a thing of the past.
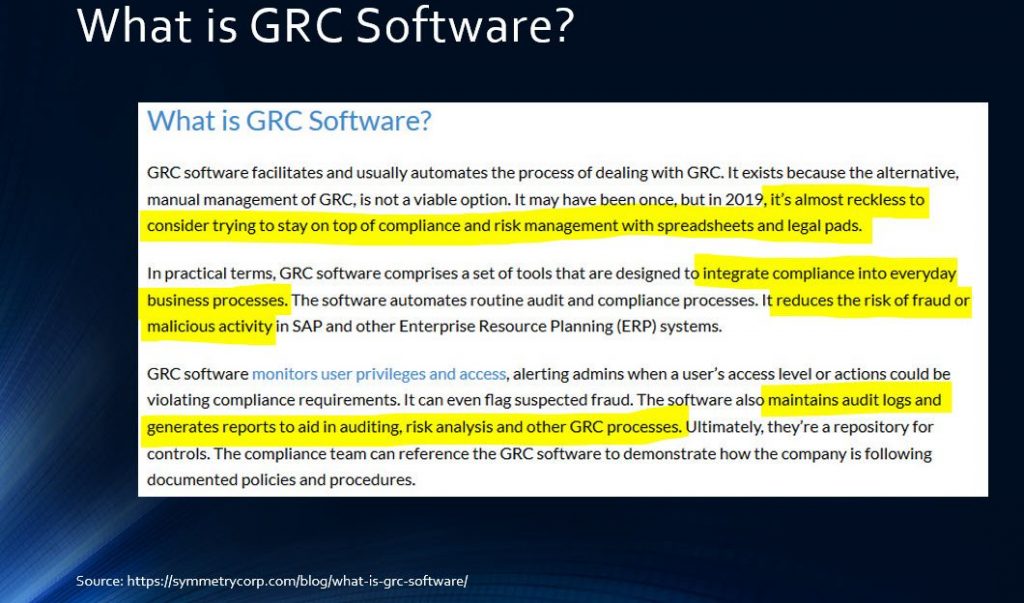
It’s important to understand your goals with GRC software. As you can see in Slide A, I highlighted several sections in my presentation. You need to focus on “integrating compliance into everyday business processes.” This is not scalable with a manual process. In addition to the processes you’ve built, Excel doesn’t offer you the same level of audit logging, fraud risk reduction, impedance on malicious activity, and a high level of easy reporting.
To help you feel at ease, the GRC industry has been growing. What does that mean? It means competition in the space. You don’t have to think about those $1 million implementations anymore. What if I told you several new companies exist and can provide these great services and cost less than $75,000 a year?
Do your research into this list of known, growing, successful GRC products. I can personally attest for these as the people that set me on that path to look at them have valuable credibility with me. I reviewed each of these and they will easily handle what you need.
Not only do they work well, but they are heavily created to empower you in their utilization. There’s no more need to worry about paying consultants that are experts in the product to create custom code. These products focus more on user experience and ensuring you can customize it to your needs without headache.
The above list is not exclusive, only what I can attest to. There are many other vendors in this space worth looking into. In addition, it’s worth inquiring whether any of your existing vendors offer GRC solutions (as a bolt-on or stand-alone). This may tie will into other processes you have and save money due to bundling products.
Why you need it
Now that we have a good understanding and comfortability that this path is both achievable and affordable, let’s break down some of those earlier questions and solve the common use cases.
Mapping
Mapping is the process of connecting your Frameworks to your Standards, your Guidelines to your Controls, your Policies to your Procedures, your Risks to your Compliance Statuses, and every other conceivable combination to develop a comprehensive GRC program. GRC Software does this inherently, it’s one of the main reasons these products exist. As seen in Slide B, it offers the ideal path, similar to the most efficient routing to visit all 50 state capitals. It offers optimal performance, quick results, is completely performed in the product (offsite, not your full-time engineer’s (FTE) time). You can quickly correlate your entire GRC environment in under an hour.
Mapping also includes the ability to quickly understand your compliance levels to known regulations, standards, and more. These products know how NIST maps to ISO and how ISO maps to HIPAA. By filling in your controls as you implement ISO, you will be able to click a button and immediately know how compliant you are with PCI DSS. How long would that take in spreadsheets? As also seen in Slide B, I guesstimated at least a full week of labor time.

Workflow Management
This is the big one that you need to spend time on talking about. Executives are going to attract to this point more than any other. Your policies are going to contain procedures. Those procedures need to be tracked. Your controls need to be tracked for your internal audits. You also have a risk register and that needs to be tracked, especially how you are working towards mitigating the listed risks (earlier mentioned POA&M). As seen in Slide C, I presented the benefits of doing this in a GRC product and its ties to mapping. Being able to look at a risk and immediately view related controls and then view a policy in one location is an underrepresented benefit of moving away from manual processes.

When you’re tracking risks, you need to send out emails to stakeholders, additional reminder emails, track their responses, have an audit log of their responses, and contain the evidence within their responses. If you have 250+ controls, is Excel scaling well to handle that workflow? Sure, it’s possible. But as you can see in Slide D, I asked someone who has been working in the GRC space for awhile how much a GRC product reduced their workflow time. Their response was over 50%!

Third-Party Risk
Third-party risk is all the new hotness in GRC (wait for that fourth-party risk, it’s occasionally mentioned these days). You need to understand what your vendors are doing with your data and before you connect them to your network. Why is third-party risk the big discussion point right now? Well, it’s simply because many breaches coming out on almost a daily basis these days starts with a vendor compromise. Target really highlighted this and it’s been continuous since.
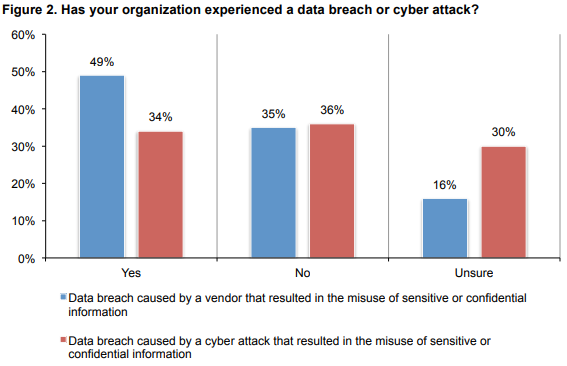
The Ponemon Institute did research in this area (April 2016) to show that it’s growing exponentially and has to be a main concern of any organization. In Figure A, you can see that 49% of the respondents that said they experienced a data breach or cyber attack said it was caused through a vendor. Even scarier, 16% of respondents are unsure if a vendor they work with that has their data had experienced a data breach or cyber attack.
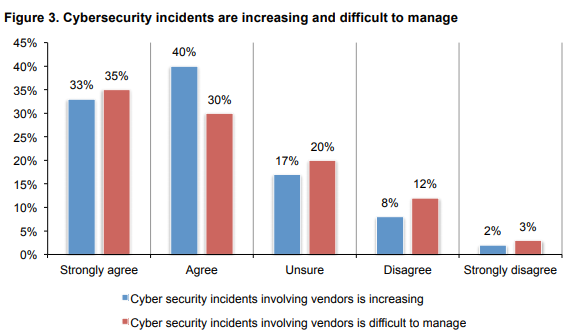
Furthermore, in Figure B, respondents (Reminder: This was April 2016; It’s November 2020 now.) stated almost across the board – 73% – that they Strongly Agree or Agree that cyber incidents involving vendors is increasing.
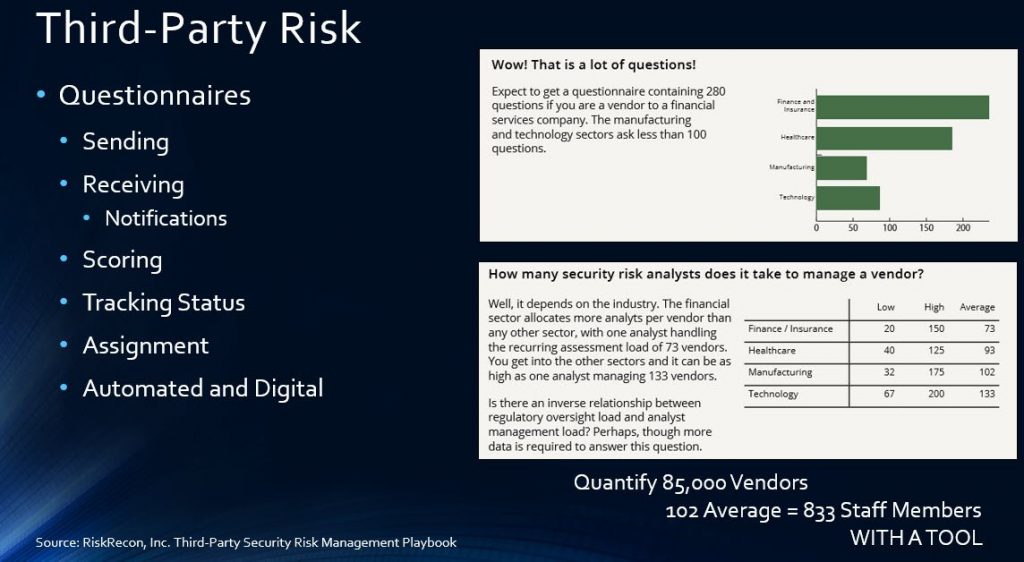
Performing third-party risk management is a hefty ask. You may have over a thousand vendors. Do you even know how many vendors your ENTIRE organization works with, not just IT? Once you understand your vendor landscape, now you need to send them questionnaires so you can properly appropriate risk quantification on them. Not just once, but on a continual cadence. As seen in Slide E, questionnaires can contain anywhere from 70 to 280 questions. Analysts have to take back those answers and score them.
I worked for a North American General Contractor. Do you want to know how many vendors they worked with? Over 85,000
– Frank McGovern
I worked for a North American General Contractor. Do you want to know how many vendors they worked with? Over 85,000 was the estimate by the risk department. Also seen in Slide E, according to a study done by RiskRecon, Inc. with the organizations they questioned doing third-party risk management, 1 risk analyst is hired to manage every 73 to 133 vendors. Quantify that with my earlier number. 85,000 vendors would be 833 risk analysts (done with the average for manufacturing industry). And that’s WITH A TOOL – aka a GRC solution. Imagine that in spreadsheets, word documents, and a SharePoint site.
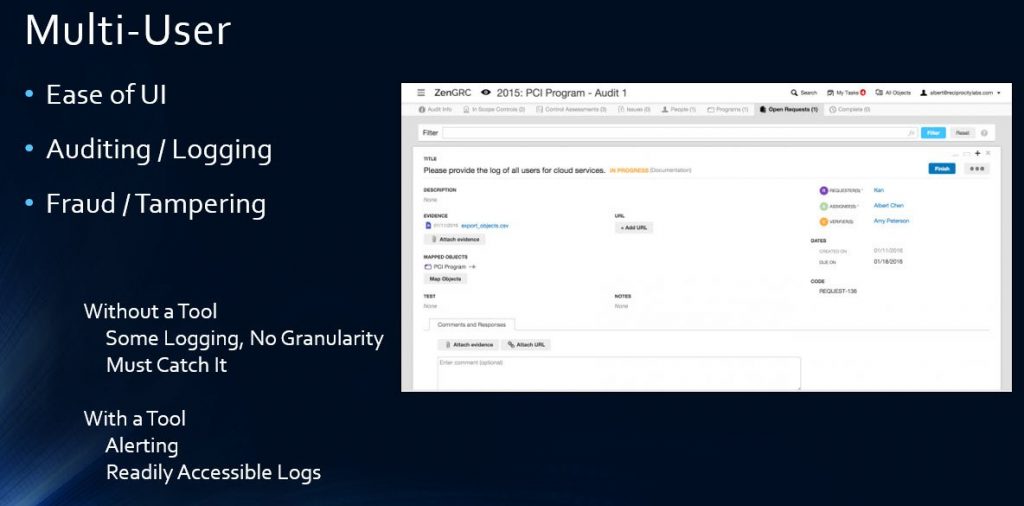
Multi-User
As your GRC processes grow, so does the workload. This workload is too much for one person. It most likely requires a team. That team needs to work together and within all the same data. A GRC product compared to spreadsheets obviously makes this a lot easier. The GRC products also have audit, logging, and tamper-resistance along for the ride. In a spreadsheet, someone can easily delete or modify a line and it may be time before it gets noticed, if it even does! Imagine if someone turns a “Non-Compliant” field to say “Compliant” because they’re tired of dealing with it. How long before you catch that inaccuracy? Probably not until another audit, what if that audit is external? Now the integrity of your self-audits and entire program are under question. SharePoint may have backups of the spreadsheet, but now you need to find it. As seen in Slide F, I discussed these points.
Reporting
This one, Slide G can do the talking. It’s a good assumption that GRC products have much better reporting and don’t require you building them manually. That’s more FTE time freed up.
Business Continuity / Disaster Recovery
This is another area that can be tracked outside of a GRC product, but is still a value add and has benefits of being included. As seen in Slide H, it just aids in your efforts of having a central repository tracking your implementation and compliance. It also gives you a place to track your table-top exercises and those lessons learned.
From there, we utilize the power of mapping again! Imagine being able to document lessons learned from a test, being able to click into them and see the risks in the risk register that were highlighted, and then see the controls that fixed those risks and where they are in a policy. Talk about proving your continual maturation! You’re on a solid path.

How to get it
Take these points provided in here and drive them home with your business leadership. Fill in the presentation with use cases that exist today in your environment. Highlight those pain points in your current implementation. They know and understand workflow management. Hit that section hard. As seen in Slide I, set that agenda.

With these points and tailoring them to your environment, you should not have any issue maturing your GRC program with the implementation of a formalized GRC solution.
Credit to Steven Maske (@ITSecurity), Senior Manager of Cyber Security at YETI, for his input in this space as well as editing this article for me.